cisco:certification_topics:general
Table of Contents
General
CLI Modes
- User Execution Mode
- No configuration changes can be made in this mode. Some show commands can be issued.
- Indicated by: >
R1>
- Privileged Mode
- Very few configuration changes can be made in this mode. All show commands can be issued.
- Indicated by: #
R1>enable Password: R1#
- Global Configuration Mode
- Global level configurations can be entered
- Indicated by: (config)
R1#conf t Enter configuration commands, one per line. End with CNTL/Z. R1(config)#
- Interface Configuration Mode
- Interface specific configurations have be entered here.
- Indicated by: (config-if)
R1(config)#int lo 101 R1(config-if)#
- Other configuration modes include Router, Line, etc.
1(config)#router bgp 100 R1(config-router)#
R1(config)#line console 0 R1(config-line)#
Right to use license / Evaluation license
Software Activation on Cisco Integrated Services Routers
R1#show license Index 1 Feature: ipbasek9 Period left: Life time License Type: Permanent License State: Active, In Use License Count: Non-Counted License Priority: Medium Index 2 Feature: securityk9 Period left: Life time License Type: RightToUse License State: Active, Not in Use, EULA accepted License Count: Non-Counted License Priority: Low Index 3 Feature: datak9 Period left: Not Activated Period Used: 0 minute 0 second License Type: EvalRightToUse License State: Active, Not in Use, EULA not accepted License Count: Non-Counted License Priority: None Index 4 Feature: FoundationSuiteK9 Period left: Not Activated Period Used: 0 minute 0 second License Type: EvalRightToUse License State: Active, Not in Use, EULA not accepted License Count: Non-Counted License Priority: None Index 5 Feature: ios-ips-update Period left: Not Activated Period Used: 0 minute 0 second License Type: EvalRightToUse License State: Active, Not in Use, EULA not accepted License Count: Non-Counted License Priority: None Index 6 Feature: hseck9 Index 7 Feature: mgmt-plug-and-play Index 8 Feature: mgmt-lifecycle Index 9 Feature: mgmt-assurance Index 10 Feature: mgmt-onplus Index 11 Feature: mgmt-compliance R1#conf t Enter configuration commands, one per line. End with CNTL/Z. R1(config)#license accept end user agreement PLEASE READ THE FOLLOWING TERMS CARE . . . ACCEPT? [yes/no]: yes R1(config)# 000060: *Jun 1 17:51:36.523: %LICENSE-6-EULA_ACCEPT_ALL: The Right to Use End User License Agreement is accepted R1(config)#do show license Index 1 Feature: ipbasek9 Period left: Life time License Type: Permanent License State: Active, In Use License Count: Non-Counted License Priority: Medium Index 2 Feature: securityk9 Period left: Life time License Type: RightToUse License State: Active, Not in Use, EULA accepted License Count: Non-Counted License Priority: Low Index 3 Feature: datak9 Period left: Not Activated Period Used: 0 minute 0 second License Type: EvalRightToUse License State: Active, Not in Use, EULA not accepted License Count: Non-Counted License Priority: None Index 4 Feature: FoundationSuiteK9 Period left: Not Activated Period Used: 0 minute 0 second License Type: EvalRightToUse R1(config)#license boot suite FoundationSuiteK9 % use 'write' command to make license boot config take effect on next boot R1(config)# 000061: *Jun 1 17:54:08.271: %LICENSE-6-EULA_ACCEPTED: EULA for feature FoundationSuiteK9 1.0 has been accepted. UDI=CISCO1921/K9:FTX144000UN; StoreIndex=2:Built-In License Storage R1(config)#do wr Building configuration... [OK] R1(config)#do reload Proceed with reload? [confirm] 000062: *Jun 1 17:54:33.831: %SYS-5-RELOAD: Reload requested by console. R1#show license Index 1 Feature: ipbasek9 Period left: Life time License Type: Permanent License State: Active, In Use License Count: Non-Counted License Priority: Medium Index 2 Feature: securityk9 Period left: Life time License Type: RightToUse License State: Active, In Use License Suite: FoundationSuiteK9 License Count: Non-Counted License Priority: Low Index 3 Feature: datak9 Period left: 8 weeks 3 days Period Used: 1 minute 52 seconds License Type: EvalRightToUse License State: Active, In Use License Suite: FoundationSuiteK9 License Count: Non-Counted License Priority: Low Index 4 Feature: FoundationSuiteK9 Period left: 8 weeks 3 days Period Used: 1 minute 52 seconds License Type: EvalRightToUse License State: Active, In Use License Count: Non-Counted License Priority: Low Index 5 Feature: ios-ips-update Period left: Not Activated Period Used: 0 minute 0 second License Type: EvalRightToUse License State: Active, Not in Use, EULA not accepted License Count: Non-Counted License Priority: None Index 6 Feature: hseck9 Index 7 Feature: mgmt-plug-and-play Index 8 Feature: mgmt-lifecycle Index 9 Feature: mgmt-assurance Index 10 Feature: mgmt-onplus Index 11 Feature: mgmt-complianceR1#show license feature Feature name Enforcement Evaluation Subscription Enabled RightToUse ipbasek9 no no no yes no securityk9 yes yes no yes yes datak9 yes yes no yes yes FoundationSuiteK9 yes yes no yes yes ios-ips-update yes yes yes no yes hseck9 yes no no no no mgmt-plug-and-play yes no no no no mgmt-lifecycle yes no no no no mgmt-assurance yes no no no no mgmt-onplus yes no no no no mgmt-compliance yes no no no no Feature name Enforcement Evaluation Subscription Enabled RightToUse
R1#show version Cisco IOS Software, C1900 Software (C1900-UNIVERSALK9-M), Version 15.5(3)M2, RELEASE SOFTWARE (fc1) Suite License Information for Module:'c1900' -------------------------------------------------------------------------------- Suite Suite Current Type Suite Next reboot -------------------------------------------------------------------------------- FoundationSuiteK9 FoundationSuiteK9 EvalRightToUse FoundationSuiteK9 securityk9 datak9 Technology Package License Information for Module:'c1900' ------------------------------------------------------------------------ Technology Technology-package Technology-package Current Type Next reboot ------------------------------------------------------------------------ ipbase ipbasek9 Permanent ipbasek9 security None None None data None None None- You must reboot for a new license to take effect.
- To install a license:
R1#license install flash:license-file.lic
SNMP Basics
- Simple Network Management Protocol (SNMP) is basically an Application Layer protocol that can be used to gather device data. This data can include interface status, protocol status, or anything else with a management information base defined (MIB).
- Devices that can send and receive messages from MIBs are called network management stations (NMS). Some examples of NMS are Cisco Prime, Solarwinds, Netcool, etc.
- Now to get a little bit more technical, the messages include GET, SET, TRAP, and REPLY.
- Messages
- GET messages are sent when the NMS periodically polls the SNMP agent which is located on the end device, such as a router.
- REPLY messages are sent from the agent to the manager in response to a GET message.
- SET messages contain configurations for the agents to use.
- TRAP messages are sent by the agent when an event is triggered on the agent. This is an unsolicited message.
- SNMP versions
- SNMPv1
- UDP
- Plan-text authentication only with community strings
- SNMPv2
- TCP/UDP
- Plan-text authentication only with community strings
- Introduces a new message labeled: GET-BULK, which concatenates multiple GET requests in one message.
- Agent can send an INFORM message which allows greater detailed error messages.
- SNMPv3
- TCP/UDP
- MD5/SHA authentication
- DES/DES-256 encryption for data integrity of messages
- GET-BULK, which concatenates multiple GET requests in one message.
- Agent can send an INFORM message which allows greater detailed error messages.
- MIB (Management Information Base)
- A database on the agent that contains managed objects, or variables, which can be set or read to provide information on network devices and interfaces.
- MIBs may come from various sources:
- Standard - The IETF standards track at Proposed, Draft, or full standard.
- Internet Draft MIB, which usually means an IETF Working Group is working on it.
- Cisco-Cisco enterprise-specific (also called proprietary or private, even though publicly documented). Such MIBs add instrumentation not covered by standard MIBs.
- Other companies- non-Cisco enterprise-specific.
- There are RFCs that contain common public variables and most organizations add their own MIBs, called Organizational IDs (OIDs).
SNMP Configuration
- Configure trap destination
- Enable SNMP r/w access to the agent (router)
- (optional) Define SNMP location/contact details
- (optional) Define an ACL to define SNMP access between the agent and NMS
SNMPv1 Configuration
R1(config)#snmp-server community TST RO R1(config)#snmp-server enable traps R1(config)#snmp-server host 192.168.1.80 TST !optional
- This is the bare configuration needed for version 1 to work with PRTG auto-discovery
- Community String: TST
- SNMP Port on PRTG server: 161
- After initial auto-discovery:
- After Gig 0/0 is admin-shut:
SNMPv2c Configuration
R1(config)#snmp-server community TST RO R1(config)#snmp-server enable traps R1(config)#snmp-server host 192.168.1.80 version 2c TST
- This is the bare configuration needed for version 2c to work with PRTG auto-discovery
- Community String: TST
- SNMP Port on PRTG server: 161
- After initial auto-discovery:
- After Gig 0/0 is admin-shut:
SNMPv3 Configuration
R1(config)#snmp-server group TSTGRP v3 noauth read TSTVIEW R1(config)#snmp-server view TSTVIEW mib-2 included R1(config)#snmp-server enable traps R1(config)#snmp-server host 192.168.1.80 version 3 noauth TST
- This is the bare configuration needed for version 3, noauth to work with PRTG auto-discovery
- Authentication Type: MD5
- User: TST
- Password: <blank>
- Encryption Type: DES
- SNMP Port on PRTG server: 161
- After initial auto-discovery:
Syslog Basics
- Syslog messages are messages that contain information about a device's hardware/software status. This can include power supply issues, routing protocol status, user's logging in/out, failed password attempts, etc.
- Network devices have various destinations that syslog messages can be sent to:
- Console line (default on)
- Logging buffer (default on)
- Terminal lines (default off)
- Syslog server
- A syslog server is used to store messages from a device's internal buffer.
- A syslog server also can add timestamps to those messages.
- A syslog server can display, sort, and search messages allowing efficient troubleshooting in performing root-cause analysis.
- Logging to the console is generally not recommended for larger syslog outputs such as Cisco's –show tech-support– output that can contain thousands of lines of code. Messages logged to the console are stored in RAM and just like a computer, the more RAM consumed, the slower the device can get. If enough RAM is consumed, the device can crash either hardware or software, leading to a cold reboot as the only option for recovery.
- Timestamp messages have various formats.
- Seq no: Once configured, adds a sequence number to messages.
- Timestamp: Once configured, adds a date and time are added to messages.
- Facility: Determines which process of the device that created the message. See RFC 5424
- Severity: The degree of the message, indicated by levels 0 through 7.
- 0: Emergency - System is unusable.
- 1: Alert - Immediate action is needed.
- 2: Critical - Critical condition.
- 3: Error - Error condition.
- 4: Warning - Warning condition.
- 5: Notification - Normal, but significant condition.
- 6: Informational - Normal, informational messages.
- 7: Debugging - Debugging message.
R1(config)#logging ? Hostname or A.B.C.D IP address of the logging host buffered Set buffered logging parameters buginf Enable buginf logging for debugging cns-events Set CNS Event logging level console Set console logging parameters count Count every log message and timestamp last occurance delimiter Append delimiter to syslog messages discriminator Create or modify a message discriminator dmvpn DMVPN Configuration esm Set ESM filter restrictions exception Limit size of exception flush output facility Facility parameter for syslog messages filter Specify logging filter history Configure syslog history table host Set syslog server IP address and parameters message-counter Configure log message to include certain counter value monitor Set terminal line (monitor) logging parameters on Enable logging to all enabled destinations origin-id Add origin ID to syslog messages persistent Set persistent logging parameters queue-limit Set logger message queue size rate-limit Set messages per second limit reload Set reload logging level server-arp Enable sending ARP requests for syslog servers when first configured snmp-trap Set syslog level for sending snmp trap source-interface Specify interface for source address in logging transactions trap Set syslog server logging level userinfo Enable logging of user info on privileged mode enablingR1(config)#logging console ? <0-7> Logging severity level alerts Immediate action needed (severity=1) critical Critical conditions (severity=2) debugging Debugging messages (severity=7) discriminator Establish MD-Console association emergencies System is unusable (severity=0) errors Error conditions (severity=3) filtered Enable filtered logging guaranteed Guarantee console messages informational Informational messages (severity=6) notifications Normal but significant conditions (severity=5) warnings Warning conditions (severity=4) xml Enable logging in XML <cr>
R1(config)#logging buffered ? <0-7> Logging severity level <4096-2147483647> Logging buffer size alerts Immediate action needed (severity=1) critical Critical conditions (severity=2) debugging Debugging messages (severity=7) discriminator Establish MD-Buffer association emergencies System is unusable (severity=0) errors Error conditions (severity=3) filtered Enable filtered logging informational Informational messages (severity=6) notifications Normal but significant conditions (severity=5) warnings Warning conditions (severity=4) xml Enable logging in XML to XML logging buffer <cr>
- In order to disable logging:
no logging console
no logging buffered
- In order to view the logs on the router:
R1#show logging Syslog logging: enabled (0 messages dropped, 2 messages rate-limited, 0 flushes, 0 overruns, xml disabled, filtering disabled) No Active Message Discriminator. No Inactive Message Discriminator. Console logging: level debugging, 36 messages logged, xml disabled, filtering disabled Monitor logging: level debugging, 0 messages logged, xml disabled, filtering disabled Buffer logging: level debugging, 36 messages logged, xml disabled, filtering disabled Exception Logging: size (4096 bytes) Count and timestamp logging messages: disabled Persistent logging: disabled No active filter modules. Trap logging: level informational, 39 message lines logged Logging Source-Interface: VRF Name: Log Buffer (8192 bytes): *Jan 2 00:00:02.247: %SMART_LIC-6-AGENT_READY: Smart Agent for Licensing is initialized *Jan 2 00:00:02.395: %IOS_LICENSE_IMAGE_APPLICATION-6-LICENSE_LEVEL: Module name = c1900 Next reboot level = ipbasek9 and License = ipbasek9 *May 17 04:13:42.127: c3600_scp_set_dstaddr2_idb(184)add = 80 name is Embedded-Service-Engine0/0 *May 17 04:13:55.703: %ESWMRVL_FLTMG-5-NOTICE: Notice: FPGA Rev 0x27 *May 17 04:13:56.931: %ESWMRVL_FLTMG-5-NOTICE: Notice: FPGA Rev 0x27 *May 17 04:14:04.595: %LINK-3-UPDOWN: Interface GigabitEthernet0/0, changed state to up *May 17 04:14:04.595: %LINK-3-UPDOWN: Interface GigabitEthernet0/1, changed state to down *May 17 04:14:05.595: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/0, changed state to up *May 17 04:14:05.595: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/1, changed state to down
- Send all logs to a designated syslog server:
R1(config)#logging host 192.168.1.205
- Set logging level:
R1(config)#logging trap ? <0-7> Logging severity level alerts Immediate action needed (severity=1) critical Critical conditions (severity=2) debugging Debugging messages (severity=7) emergencies System is unusable (severity=0) errors Error conditions (severity=3) informational Informational messages (severity=6) notifications Normal but significant conditions (severity=5) warnings Warning conditions (severity=4) <cr>
- Optional parameters would be (timestamps are enabled by default):
- Add sequence numbers:
R1(config)#service sequence-numbers
- Set trap destination:
R1(config)#logging source-interface gigabitEthernet 0/1
IPSLA for troubleshooting
- IPSLA is Internet Protocol Service Level Agreement.
- Cisco proprietary.
- Utilizes ICMP echo tests to ping a distant IP which is done through various IPSLA messages.
- IPSLA can measure end-to-end performance for determining packet loss, latency, and response time.
- Steps to configure IPSLA:
R1(config)#ip sla 101 R1(config-ip-sla)#icmp-echo 192.168.1.1 source-interface g0/0 ! source-interface is optional
- Verify IP SLA configuration and operation
R1#show ip sla configuration IP SLAs Infrastructure Engine-III Entry number: 101 Owner: Tag: Operation timeout (milliseconds): 5000 Type of operation to perform: icmp-echo Target address/Source interface: 192.168.1.1/GigabitEthernet0/0 Type Of Service parameter: 0x0 Request size (ARR data portion): 28 Data pattern: 0xABCDABCD Verify data: No Vrf Name: Schedule: Operation frequency (seconds): 10 (not considered if randomly scheduled) Next Scheduled Start Time: Start Time already passed Group Scheduled : FALSE Randomly Scheduled : FALSE Life (seconds): Forever Entry Ageout (seconds): never Recurring (Starting Everyday): FALSE Status of entry (SNMP RowStatus): Active Threshold (milliseconds): 5000 Distribution Statistics: Number of statistic hours kept: 2 Number of statistic distribution buckets kept: 1 Statistic distribution interval (milliseconds): 20 Enhanced History: History Statistics: Number of history Lives kept: 0 Number of history Buckets kept: 15 History Filter Type: None
R1#show ip sla statistics IPSLAs Latest Operation Statistics IPSLA operation id: 101 Latest RTT: 1 milliseconds Latest operation start time: 18:47:15 UTC Mon Jun 1 2020 Latest operation return code: OK Number of successes: 7 Number of failures: 0 Operation time to live: Forever
Device Configuration Management
- In IOS, device configuration changes are stored in RAM, inside a file call running-configuration. These changes are volatile unless saved in NVRAM or some other location using the following commands:
R1#copy running-config startup-config Destination filename [startup-config]? Building configuration... [OK] R1#copy run start Destination filename [startup-config]? Building configuration... [OK] R1#write memory Building configuration... [OK] R1#wr Building configuration... [OK]
External Backups
- A TFTP server can used to create/restore backups of configuration/image files.
R1#copy start R1#copy startup-config tftp Address or name of remote host []? 192.168.1.205 Destination filename [r1-confg]? .!! 5372 bytes copied in 4.060 secs (1323 bytes/sec)
R1#copy tftp running-config Address or name of remote host []? 192.168.1.205 Source filename []? r1-confg Destination filename [running-config]? Accessing tftp://192.168.1.205/r1-confg... Loading r1-confg from 192.168.1.205 (via GigabitEthernet0/0): ! [OK - 5372 bytes] 000041: *Jun 2 12:51:08.227: %SYS-5-CONFIG_I: Configured from tftp://192.168.1.205/r1-confg by console
- Additionally, a device can boot off of configuration/image files stored on a TFTP server.
R1(config)#boot system tftp image.bin 192.168.1.205
R1(config)#boot network tftp r1-confg 192.168.1.205
Cisco Discovery Protocol (CDP) and Link Layer Device Protocol (LLDP)
- CDP is a Cisco proprietary protocol to collect information about locally attached devices.
- LLDP is a IEEE standards based protocol to collect information about locally attached devices.
- Both operate at layer 2.
- CDP is enabled by default on IOS devices. Here are two examples for disabling CDP, then enabling it:
R1(config)#no cdp run R1(config)#do show cdp neighbors % CDP is not enabled R1(config)#cdp run
- LLDP is disabled by default on IOS devices. Here are two examples for enabling LLDP, then disabling it:
R1(config)#lldp run R1(config)#no lldp run R1(config)#do show lldp neighbors % LLDP is not enabled
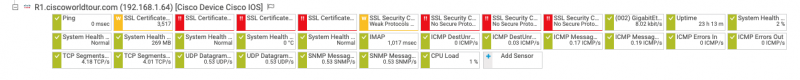
R1#show cdp neighbors Capability Codes: R - Router, T - Trans Bridge, B - Source Route Bridge S - Switch, H - Host, I - IGMP, r - Repeater, P - Phone, D - Remote, C - CVTA, M - Two-port Mac Relay Device ID Local Intrfce Holdtme Capability Platform Port ID homeswitch.ciscoworldtour.com Gig 0/0 126 R S I WS-C3750X Gig 2/0/7 Total cdp entries displayed : 1R1#show lldp neighbors Capability codes: (R) Router, (B) Bridge, (T) Telephone, (C) DOCSIS Cable Device (W) WLAN Access Point, (P) Repeater, (S) Station, (O) Other Device ID Local Intf Hold-time Capability Port ID homeswitch.ciscoworlGi0/0 120 B,R Gi2/0/7 Total entries displayed: 1- Default CDP options are:
R1(config)#do show cdp Global CDP information: Sending CDP packets every 60 seconds Sending a holdtime value of 180 seconds Sending CDPv2 advertisements is enabled
- To change the CDP timer:
R1(config)#cdp timer 30 R1(config)#do show cdp Global CDP information: Sending CDP packets every 30 seconds
- To change the CDP holdtime:
R1(config)#cdp holdtime 90 R1(config)#do show cdp Global CDP information: Sending a holdtime value of 90 seconds
- LLDP options can be changed the same way CDP. I won't repeat the commands here, just replace cdp with lldp.
- To see more details on neighbors:
R1#show cdp neighbors detail ------------------------- Device ID: homeswitch.ciscoworldtour.com Entry address(es): Platform: cisco WS-C3750X-48P, Capabilities: Router Switch IGMP Interface: GigabitEthernet0/0, Port ID (outgoing port): GigabitEthernet2/0/7 Holdtime : 136 sec Version : Cisco IOS Software, C3750E Software (C3750E-UNIVERSALK9-M), Version 15.2(4)E8, RELEASE SOFTWARE (fc3) Technical Support: http://www.cisco.com/techsupport Copyright (c) 1986-2019 by Cisco Systems, Inc. Compiled Fri 15-Mar-19 09:00 by prod_rel_team advertisement version: 2 VTP Management Domain: '' Native VLAN: 1 Duplex: full Total cdp entries displayed : 1
homeswitch#show cdp neighbors detail ------------------------- Device ID: R1 Entry address(es): IP address: 192.168.1.64 Platform: Cisco CISCO1921/K9, Capabilities: Router Source-Route-Bridge Switch Interface: GigabitEthernet2/0/7, Port ID (outgoing port): GigabitEthernet0/0 Holdtime : 64 sec Version : Cisco IOS Software, C1900 Software (C1900-UNIVERSALK9-M), Version 15.5(3)M2, RELEASE SOFTWARE (fc1) Technical Support: http://www.cisco.com/techsupport Copyright (c) 1986-2016 by Cisco Systems, Inc. Compiled Sun 07-Feb-16 02:36 by prod_rel_team advertisement version: 2 Duplex: full Management address(es): IP address: 192.168.1.64 Total cdp entries displayed : 1
- Using CDP and LLDP, you can map a network topology without having to physically trace cables.
Misc
Timezone
- To change the timezone to 6 hours more than UTC:
R1(config)#clock timezone zone 6 0 000044: *Jun 2 15:21:13.750: %SYS-6-CLOCKUPDATE: System clock has been updated from 15:21:13 UTC Tue Jun 2 2020 to 21:21:13 zone Tue Jun 2 2020, configured from console by console. R1(config)#do show clock *21:21:22.906 zone Tue Jun 2 2020
- To change the timezone to UTC:
R1(config)#no clock timezone 000045: *Jun 2 15:22:45.942: %SYS-6-CLOCKUPDATE: System clock has been updated from 21:22:45 zone Tue Jun 2 2020 to 15:22:45 UTC Tue Jun 2 2020, configured from console by console. R1(config)#do show clock *15:22:49.898 UTC Tue Jun 2 2020
Loopbacks
- Loopback interfaces are logical interfaces. By default, they are up/up. Loopbacks can be admin shut.
- Loopbacks never go down unless there is a hardware, software, or user action.
- An example of a hardware failure would be a device losing power.
- An example of a software failure would be the image file getting corrupted.
- An example of a user action would be a user manually issuing a shutdown command, changing the interface status to admin shut.
- To create a loopback:
R1(config)#int lo ? <0-2147483647> Loopback interface number <0-2> LongReachEthernet interface number R1(config)#int lo 101 000046: *Jun 2 15:38:04.562: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback101, changed state to up R1(config-if)#do show ip int bri | i 101 Loopback101 unassigned YES unset up up
- When a loopback is admin shut:
R1(config-if)#shut 000047: *Jun 2 15:39:13.074: %LINK-5-CHANGED: Interface Loopback101, changed state to administratively down 000048: *Jun 2 15:39:14.074: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback101, changed state to down R1(config-if)#do show ip int bri | i 101 Loopback101 unassigned YES unset administratively down down
- To add an IP address to Loopback 101:
R1(config-if)#ip address 172.16.24.101 255.255.255.255 R1(config-if)#no shut R1(config-if)#do show ip int brief 000049: *Jun 2 15:41:58.710: %LINK-3-UPDOWN: Interface Loopback101, changed state to up 000050: *Jun 2 15:41:59.710: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback101, changed state to up R1(config-if)#do show ip int brief | i 101 Loopback101 172.16.24.101 YES manual up up
Cisco IOS Upgrades
- Upgrading a Cisco device is relatively easy and straightforward. There are additional options that can be used and I'll cover them below too.
- Copying an image from a TFTP server works if the image is small in size. Generally, I would say anything greater than 40 Megabytes should not be used for TFTP transfer, unless you have to.
- I would recommend that you use a FTP (SFTP), USB drive, or flash card. Copy the image to the FTP server, or other source, then copy the image from the source to the device. Usually, you would do this on the command line.
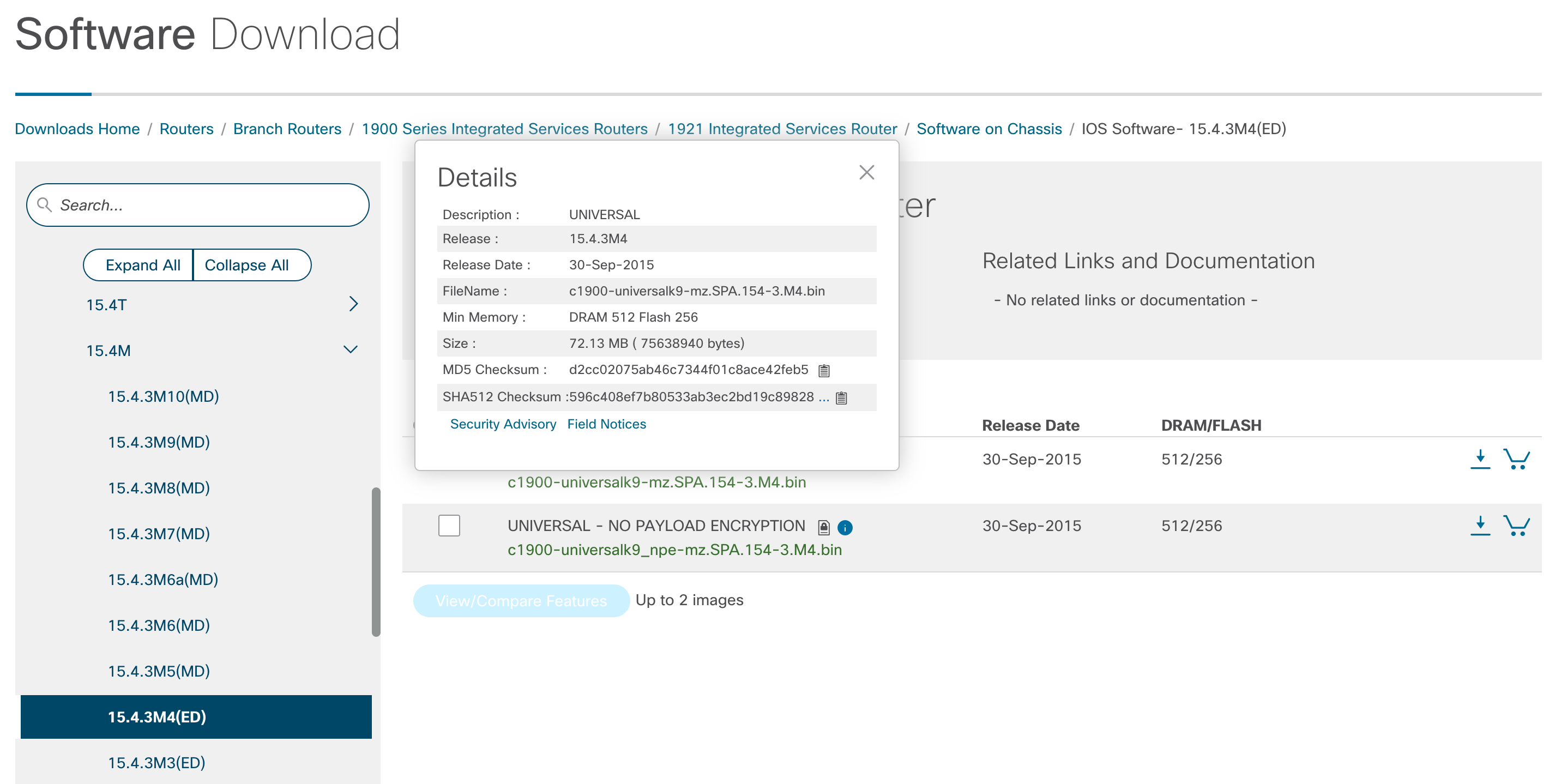
- Download the software image from Cisco's website:
- Example of copying from a TFTP server to a Cisco 1921 router:
R1#copy tftp flash Address or name of remote host []? 192.168.1.205 Source filename []? c1900-universalk9-mz.SPA.154-3.M4.bin Destination filename [c1900-universalk9-mz.SPA.154-3.M4.bin]? Accessing tftp://192.168.1.205/c1900-universalk9-mz.SPA.154-3.M4.bin... Loading c1900-universalk9-mz.SPA.154-3.M4.bin from 192.168.1.205 (via GigabitEthernet0/0): !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!O!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!O!!!!!!!!!!!!O!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! [OK - 75638940 bytes] 75638940 bytes copied in 120.840 secs (625943 bytes/sec)
- Then do an MD5 file integrity verify (success):
R1#verify /md5 flash:c1900-universalk9-mz.SPA.154-3.M4.bin d2cc02075ab46c7344f01c8ace42feb5 ...........................A lot of dots ........... .....MD5 of usbflash0:c1900-universalk9-mz.SPA.154-3.M4.bin Done! Verified (usbflash0:c1900-universalk9-mz.SPA.154-3.M4.bin) = d2cc02075ab46c7344f01c8ace42feb5
- Then do an MD5 file integrity verify (failure):
R1#verify /md5 flash:c1900-universalk9-mz.SPA.154-3.M4.bin d2cc02075ab46c7344f01c8ace42feb ...........................A lot of dots ........... .....MD5 of usbflash0:c1900-universalk9-mz.SPA.154-3.M4.bin Done! %Error verifying usbflash0:c1900-universalk9-mz.SPA.154-3.M4.bin Computed signature = d2cc02075ab46c7344f01c8ace42feb5 Submitted signature = d2cc02075ab46c7344f01c8ace42feb
- Validate that the Configure Register is set correctly:
R1#show version | i regist Configuration register is 0x2102
- To copy from an FTP server:
R1#copy ftp flash Address or name of remote host [192.168.1.205]? Source filename [c1900-universalk9-mz.SPA.154-3.M4.bin]? Destination filename [c1900-universalk9-mz.SPA.154-3.M4.bin]? Accessing ftp://192.168.1.205/c1900-universalk9-mz.SPA.154-3.M4.bin... Loading c1900-universalk9-mz.SPA.154-3.M4.bin !!!!!!!!!!!!! A lot of exclamation points !!!! [OK - 75638940/4096 bytes] 75638940 bytes copied in 95.408 secs (792795 bytes/sec)
- Don't forget to perform a file verify as detailed above.
- Optionally, if there are more than one image stored on the device's flash, then use the boot system command.
R1(config)#boot system usbflash0 c1900-universalk9-mz.SPA.154-3.M4.bin R1(config)#do show run | i boot boot-start-marker boot system usbflash0 c1900-universalk9-mz.SPA.154-3.M4.bin boot-end-marker license boot suite FoundationSuiteK9 R1(config)#end R1#wr Building configuration... 000054: *Jun 2 18:14:01.361: %SYS-5-CONFIG_I: Configured from console by console[OK] R1#reload Proceed with reload? [confirm] 000055: *Jun 2 18:14:42.013: %SYS-5-RELOAD: Reload requested by console. Reload Reason: Reload Command. R1#show version Cisco IOS Software, C1900 Software (C1900-UNIVERSALK9-M), Version 15.4(3)M4, RELEASE SOFTWARE (fc1) Technical Support: http://www.cisco.com/techsupport Copyright (c) 1986-2015 by Cisco Systems, Inc. Compiled Sun 27-Sep-15 05:31 by prod_rel_team ROM: System Bootstrap, Version 15.0(1r)M9, RELEASE SOFTWARE (fc1) R1 uptime is 2 minutes System returned to ROM by reload at 18:14:40 UTC Tue Jun 2 2020 System image file is "usbflash0:c1900-universalk9-mz.SPA.154-3.M4.bin"
- Industry best practice is to keep a backup image on the device's flash in case the primary flash gets corrupted or there is a bug. It is easier and more efficient to revert to a previous known-good image that is stored on the device's flash, than to have to copy it from a backup server or other source.
SPAN
Local SPAN
- SPAN is when a port is designated to duplicate all defined traffic out a certain port. This is useful when traffic is to be captured via a sniffer. As with all things Cisco, this definition is an over-simplification and is to be used just as general terminology at the CCNA level.
- I have used this feature many times in business to determine the root-cause of an issue. I would consider this as a must know and lab it out many times over.
- There are different ways to implement SPAN, and since this is the Local SPAN section, only Local SPAN will be discussed.
- Depending on the IOS version and switch model, will depend on the exact commands needed to successfully implement Local SPAN.
- The following example is from a Cisco 3705x Switch, running IOS version 15.2(4)E8 (c3750e-universalk9-mz.152-4.E8.bin)
- Source port: Gig 2/0/17 (all traffic from this port will be duplicated to the destination port.)
- Destination port: Gig 2/0/4 (all traffic sent to this port will be forwarded to the sniffer.)
monitor session 1 source interface gigabitEthernet 2/0/17 homeswitch(config)#$sion 1 destination interface gigabitEthernet 2/0/4
homeswitch#show monitor session 1 Session 1 --------- Type : Local Session Source Ports : Both : Gi2/0/17 Destination Ports : Gi2/0/4 Encapsulation : Native Ingress : Disabled
Network Programmability
- Currently, to configure networking devices, it is a very laborious process. Simple scripts can be written with flat files, just as Microsoft Excel, but that still consumes a lot of man-power. A solution to this, that is currently on the market, is network programmability or Software Defined Network (SDN).
- SDN takes advantage of APIs and how they interact with the Data and Control planes.
- APIs are Application Programming Interface. An example of an API is a Google Map that is embedded into webpages. Of course, that example isn't reflective of SDN, but I wanted to start with something that most people would be able to be relate to.
- On a physical device, the Data plane, or forwarding plane, is responsible for forwarding frames of packets from its ingress to egress interfaces using protocols managed in the control plane.
- On a physical device, the Control plane, is responsible for managing and controlling any forwarding table that the data plane uses. For example, routing protocols are all managed by the control plane.
- On a physical device, there is also the Management plane, but that won't be discussed in this section.
- SDN removes the control plane intelligence from the network devices by utilizing a central controller to manage the network. SDN can in turn, automate configurations and remediation of all devices.
- This means that the SDN controller now centrally controls all device Control planes. APIs can be used to control and configure the network without human intervention. Rise of the Machines!
- In terms of SDN, the Data (or forwarding) plane contains network elements that are any combination of virtual and physical that process traffic.
- In terms of SDN, the Control plane is a software solution where SDN controllers reside.
- A new SDN plane is added, called the Application plane. The Application plane contain the applications that communicate their network requirements toward the controller using APIs.
- In summary, applications instruct the network what to do based on business needs instead of human interventions, which now only takes minutes to complete tasks, instead of weeks.
Northbound and Southbound APIs
- Communication with the data plane is defined with southbound interfaces.
- Services offered to the application plane using the northbound interface.
Southbound APIs
- Allows two devices to communicate between the controllers and network devices. Southbound APIs have many standards and will be discussed next.
- OpenFlow is an industry-standard API that can be used to configure white label switches and as a result, it defines the flow path through the network. All the configuration is completed through NETCONF.
- NETCONF is a network management protocol standardized by the IETF which the configuration of networking devices can be installed, modified, and deleted using XML.
- onePK is a Cisco proprietary SBI (Southbound Interface) that allows the inspection/modification of network configs without hardware upgrades.
- OpFlex is an SBI that is an open-standard distributed control system.
Northbound APIs
- Are used to communicate from the SDN controller to the applications running over the network.
- The NBIs (Northbound Interfaces) allow applications to manage and control the network by setting up a framework.
- Examples of NBIs are automated granular firewall monitoring, user identity management, and access policy control. There isn't a single NBI that can be used for all applications, therefore, many NBIs must be used to accomplish tasks.
cisco/certification_topics/general.txt · Last modified: 2020/06/03 16:47 by Derg Enterprises